In the previous article,“What Is Cyber Hygiene? A Practical Guide to Building Stronger Security Habits,” we discussed how everyday security practices shape an organization’s overall defense posture. However, understanding cyber hygiene is only the starting point. The more critical question is what happens when cyber hygiene is weak or inconsistently applied.
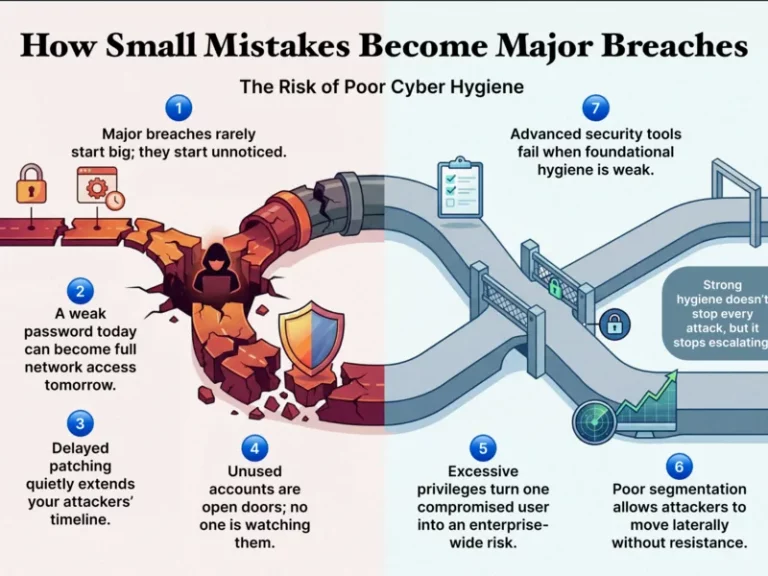
In today’s threat landscape, major breaches rarely begin with sophisticated attacks alone. They often start with small, overlooked mistakes that compound over time. Poor cyber hygiene creates conditions where these minor gaps escalate into serious security incidents.
Small Oversights Create Large Attack Opportunities
Weak passwords, delayed patching, unused accounts, misconfigured systems, and inconsistent access controls may seem manageable in isolation. Yet attackers thrive on these weaknesses. Poor cyber hygiene connects these small oversights into a chain of opportunities that enables attackers to move deeper into environments without resistance.
Once an attacker gains an initial foothold, often through phishing, credential reuse, or exposed services, poor hygiene accelerates their progress. Unmonitored systems, excessive privileges, and outdated configurations reduce the effort required to escalate access and expand impact.
How Poor Cyber Hygiene Amplifies Breach Impact
Cyber incidents become major breaches not just because attackers gain access, but because organizations lack containment controls. Poor cyber hygiene often means insufficient visibility, weak segmentation, and limited enforcement of least-privilege access. As a result, attackers are able to move laterally, access sensitive data, and persist undetected.
In many post-breach investigations, the damage was not caused by the initial compromise, but by what followed. Inconsistent hygiene practices allow attackers to remain active longer, exfiltrate more data, and disrupt more systems, turning a minor incident into a business crisis.
The Compounding Effect of Neglected Cyber Hygiene
Cyber hygiene is cumulative. When basic controls are neglected across multiple systems, the overall security posture degrades faster than expected. Organizations may believe they are protected because advanced tools are in place, but poor hygiene undermines their effectiveness.
Security technologies rely on clean foundations, accurate inventories, hardened configurations, timely updates, and disciplined access management. Without these fundamentals, even well-funded security programs struggle to prevent breaches from escalating.
From Awareness to Accountability in Cyber Hygiene
One of the key challenges highlighted since “What Is Cyber Hygiene? A Practical Guide to Building Stronger Security Habits” is that cyber hygiene often lacks ownership. When hygiene practices are treated as optional or informal, accountability disappears, and gaps multiply.
Effective cyber hygiene requires consistent enforcement, clear responsibility, and measurable outcomes. Organizations that mature beyond awareness focus on making hygiene repeatable, auditable, and aligned with risk priorities rather than relying on individual behavior alone.
Strengthening Cyber Hygiene to Prevent Breach Escalation
Improving cyber hygiene is less about adding new tools and more about reducing avoidable exposure. By tightening configurations, enforcing least privilege, monitoring continuously, and standardizing hygiene practices across environments, organizations can dramatically limit how far attackers can go, even when initial access occurs. Strong cyber hygiene does not eliminate attacks, but it prevents small mistakes from becoming enterprise-wide breaches.
At Terrabyte, we help organizations strengthen cyber hygiene by aligning foundational security practices with real-world threat behavior. Through structured, risk-driven approaches, Terrabyte supports enterprises in closing everyday gaps that attackers exploit, transforming cyber hygiene from basic discipline into a critical layer of breach prevention.