Data breaches are no longer rare, unexpected events. They have become an operational reality for modern organizations operating in cloud environments, remote work models, and interconnected digital ecosystems. While many security discussions focus on preventing breaches, a more critical question often goes unanswered: what happens to data after a breach occurs?
In a previous discussion on “What Happens After Data Leaks? Consequences Every Business Should Know,” we explored the financial, legal, and reputational damage that follows exposure. This article takes that conversation further by examining a more strategic issue: the role of persistent data protection in reducing long-term damage once perimeter defense fails.
Why Breaches Are No Longer the End of the Story
Traditional security models were built around the assumption that keeping attackers out was enough. Firewalls, intrusion prevention systems, and access controls were designed to protect systems and networks. However, modern attack techniques have made this assumption increasingly unrealistic.
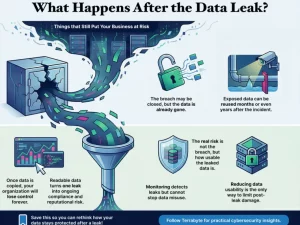
Once attackers gain access, data can be copied, exfiltrated, and reused indefinitely. Unlike systems, data does not disappear when an incident is resolved. It can be stored, sold, analyzed, or weaponized long after the initial breach is closed. This reality makes post-breach data exposure one of the most damaging aspects of modern cyber incidents.
The Limits of Incident Response Without Data Protection
Incident response plays a critical role in containing breaches, restoring systems, and resuming operations. However, response alone does not address a fundamental problem: exposed data remains valuable if it is still readable and usable.
Organizations that rely solely on access-based security often discover that even after credentials are reset and vulnerabilities are patched, sensitive information has already escaped their control. Customer records, intellectual property, internal documents, and confidential communications can continue to create risk months or even years later. This is where many security strategies fall short, not because detection failed, but because data itself was never protected independently of the system.
Shifting from System-Centric to Data-Centric Protection
Persistent data protection represents a shift in security thinking. Instead of focusing only on securing infrastructure, it emphasizes protecting the data itself, wherever it goes, and however it is accessed. This approach ensures that:
- Sensitive data remains protected even if systems are compromised
- Unauthorized access does not automatically translate into usable information
- Controls persist across endpoints, cloud platforms, and third-party environments
By applying protection directly to data, organizations reduce the long-term impact of breaches rather than only attempting to prevent them.
Reducing Post-Breach Damage Through Persistent Controls
When data is protected persistently, the consequences of a breach change significantly. Even if attackers manage to extract files or databases, encryption, access restrictions, and usage controls limit what can be done with the stolen information. This reduces:
- The likelihood of large-scale data misuse
- Regulatory exposure caused by readable data leaks
- Business disruption resulting from intellectual property loss
More importantly, it shifts security success metrics from “preventing all breaches” to limiting real-world damage when breaches occur.
Why Persistent Data Protection Supports Long-Term Resilience
Modern organizations must assume that breaches will happen at some point. The differentiator is not whether an incident occurs, but how much damage it causes. Persistent data protection aligns with this reality by focusing on resilience rather than absolute prevention.
By protecting data beyond the perimeter, organizations can maintain trust, reduce recovery costs, and sustain operations even in hostile environments. This approach supports modern security frameworks and provides a more durable foundation for enterprise risk management.
At Terrabyte, we help organizations strengthen their data protection strategies by focusing on persistent, data-centric security approaches. By aligning protection mechanisms with real-world breach scenarios, Terrabyte enables businesses to reduce post-breach impact and build long-term resilience in an increasingly complex threat landscape.