Data leaks are often treated as one-time security incidents, events that begin with a breach and end once systems are restored. In the previous article, “What Happens After Data Leaks? Consequences Every Business Should Know,” we discussed the immediate financial, legal, and reputational consequences organizations face following a data exposure.
However, the real risk does not stop when the incident response team declares the breach contained. In many cases, the most damaging effects of a data leak emerge long after the initial incident, driven by the continued exposure and reuse of compromised data.
Why Data Exposure Outlasts the Breach Itself
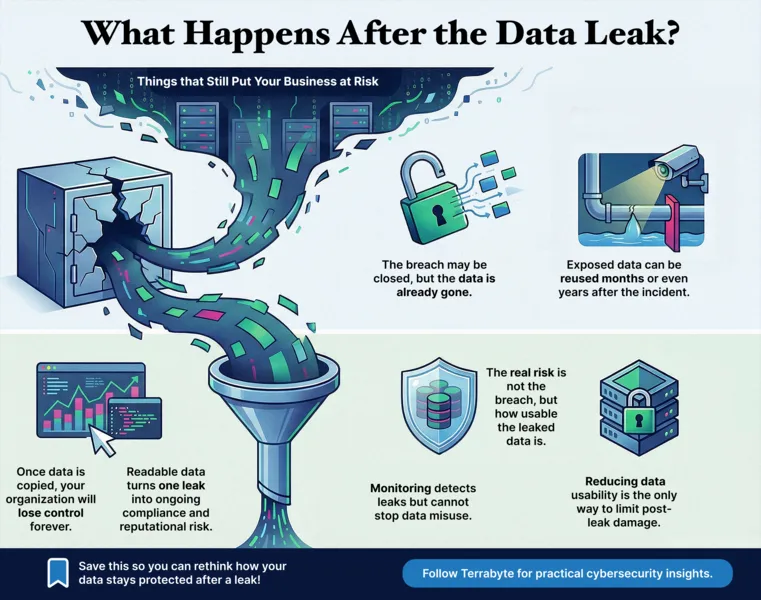
Unlike systems and infrastructure, data cannot be “patched” or reset once it has been copied. When sensitive information is leaked, it may be stored, resold, analyzed, or reused indefinitely. This persistence transforms a single security incident into an ongoing business risk.
Exposed data can surface months or even years later in fraud schemes, competitive intelligence, or targeted attacks. Customer records, internal communications, and intellectual property may continue to circulate long after the organization believes the incident has been resolved. This is why data exposure, not just the breach itself, should be the primary concern.
The Difference Between Losing Access and Losing Control
Many organizations focus their response on restoring access control: resetting credentials, closing vulnerabilities, and reinforcing perimeter defenses. While necessary, these actions do not address a more critical issue, loss of control over data.
Once data leaves the organization without protection, it can be read, duplicated, and redistributed without restriction. At this point, the organization no longer dictates how that data is used. This distinction explains why some data leaks result in limited impact, while others escalate into prolonged crises.
How Unprotected Data Amplifies Post-Leak Damage
The absence of persistent data protection significantly increases the consequences of a leak. Exposed data that remains readable and usable creates compounding risks over time. These risks often include:
- Ongoing regulatory exposure as leaked data continues to violate compliance requirements
- Long-term reputational damage when sensitive information resurfaces
- Competitive disadvantage caused by the loss of confidential business data
Without mechanisms to limit usability, data leaks evolve from isolated incidents into sustained threats.
Why Visibility Alone Is Not Enough
Modern security tools provide extensive visibility into incidents, alerts, and anomalous behavior. However, visibility does not equate to control. Knowing that data has been leaked does not prevent its misuse if the data itself lacks embedded protection.
True data protection requires enforcing controls that remain effective even when monitoring and detection have failed. This means shifting focus from observing threats to reducing the value of exposed data.
Reconsidering Data Protection Through an Exposure Lens
Viewing data protection through the lens of exposure changes how organizations measure security success. Instead of asking whether a breach occurred, the more important question becomes: how usable is the exposed data?
By prioritizing data-centric protection, organizations can ensure that even when leaks happen, the data itself remains constrained. This approach reduces the long-term impact of exposure and aligns security strategy with the realities of modern cyber risk.
At Terrabyte, we help organizations strengthen data protection by focusing on reducing data exposure and limiting post-leak damage. By aligning security strategies with how data is actually used and shared, Terrabyte supports businesses in managing long-term risk and maintaining resilience in an environment where data leaks are an ongoing reality.