
Understanding Cross-Site Scripting (XSS): What It Is, How It Happens, and How to Prevent It
In the realm of web security, Cross-Site Scripting (XSS) remains one of the most common and damaging vulnerabilities. This article

In the realm of web security, Cross-Site Scripting (XSS) remains one of the most common and damaging vulnerabilities. This article

In the ever-evolving landscape of cybersecurity threats, brute force attacks remain a prevalent method used by cybercriminals to gain unauthorized

In the realm of cybersecurity, the Man-in-the-Middle (MitM) attack is a significant threat that can compromise the integrity and confidentiality

In the realm of cybersecurity, cloud cryptomining has emerged as a significant threat to businesses and individuals using cloud services.

In the digital age, bill fraud has become an increasingly common and sophisticated type of financial crime. Understanding what bill

In today’s digital landscape, Amazon Web Services (AWS) is a leading cloud platform, providing scalable and cost-effective solutions for businesses
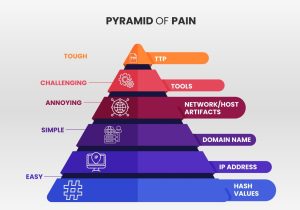
In the ever-evolving landscape of cybersecurity, the Pyramid of Pain is a crucial framework for understanding and mitigating threats. Developed

In today’s rapidly advancing technological landscape, the importance of cybersecurity in the healthcare industry cannot be overstated. With the integration

Network sniffing is a common yet potentially dangerous technique used in the realm of cybersecurity. This article will explain what