
Expose Which Attacks Can Breach Your Defenses
Company Overview
Picus Security developed transformative security validation innovations for end-to-end attack readiness, visibility, and effortless mitigation to pre-empt cyber attacks across all cyber defense layers. The Picus Security Validation Platform transforms security practices by correlating, prioritizing, and validating exposures across siloed findings – so teams can focus on critical gaps and high-impact fixes. With Picus, security teams can quickly take action with one-click mitigations to stop more threats with less effort.
Terrabyte Group partners with Picus Security to Provide Automated Cyber Security Posture Validation in Singapore
We help organisations continuously validate, measure, and enhance the effectiveness of their security controls so that they can more accurately assess risks and strengthen cyber resilience. As the pioneer of Breach and Attack Simulation (BAS), our Complete Security Control Validation Platform is used by security teams worldwide to proactively identify security gaps and obtain actionable insights to address them.
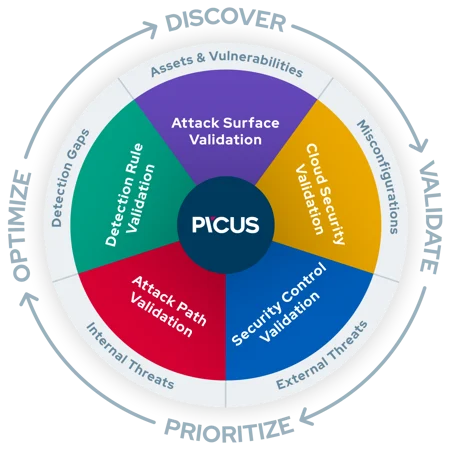
Solutions Overview
Quantify Cyber Risk
Reduce Threat Exposure
Amplify Team Impact
Products Overview
Security Control Validation
Attack Path Validation
Detection Rule Validation
Cloud Security Validation
Attack Surface Validation
Reach out to find out more
See how our solution works firsthand. Request a personalized demo and discover how it can solve your specific challenges.
